This follows from a secret report by IPCS-Black Wall Global, based on an investigation conducted by the company’s specialists, presented to the Israeli security services, a document available to Cyprus Daily News.
The report on the digital forensics investigation conducted by IPCS-BWG specialists is titled «Verification of the possibility of hacking CCTV cameras and infiltrating WhatsApp» and is dated 22.10.2023.
The October 7 attack on Israel by Hamas terrorists came as a complete surprise and raised many questions that need answers. Hamas has never been characterized by a high level of planning and technicality in its operations. Therefore, when numerous groups of Palestinian terrorists managed to stealthily approach the high-tech security fence and use bulldozers to breach it in several places, many security experts suspected that the planning of this essentially military operation and its technological support were carried out by someone outside, but not by Hamas.
Israeli authorities are conducting a comprehensive investigation into the events of October 7 and are finding increasing evidence of the involvement of other countries and organizations in Hamas’s crimes.
One of the key questions of this investigation is how the terrorists were able to approach the security fence, which is equipped with numerous surveillance cameras and various detectors, unhindered and virtually invisible to observers.
The answer to this and other questions is provided by the investigation conducted by specialists of the Digital Forensics Investigation Group-IPCS, which is a part of Black Wall Global. The investigation was led by Israel Police Chief Superintendent (ret.) Asher Ben Artzi, a counter-terrorism expert and National Security Advisor.
The IPSC, part of Black Wall Global, began operations with the retirement, after 34 years of service to the Israel Security Agency (Shin Bet), of the Director of the Israeli INTERPOL Bureau, Asher Ben Artzi, retired Chief Superintendent of the Israel Police, and focuses on intelligence, forensics, and cyber security.
Black Wall Global is a digital intelligence, cybersecurity, and defense agency founded by a group of intelligence, counterterrorism, elite unit, and law enforcement veterans. The president is Commissioner Khoo Boon Hui, former chief of police of Singapore and former president of Interpol.
CEO — Amir (Anri) David, former Senior Executive Assistant to the President of the International Bureau of Criminal Investigation CYBERPOL, a counter-terrorism expert and National Security Advisor, Academician of International Academy of Tchnological Sciences of Russia.
The Board of Directors includes Arik «Haris» Barbing, a high-ranking ISA official, Israel Security Agency (ShinBet), equal in rank to an IDF Major General, and founder and head of ShinBet’s cyber division.
The unique area in which the company specializes, along with other areas of intelligence and cybernetics, is the detection and localization of relevant areas in video recordings, including forensic digital analysis of surveillance footage using comparative forensic geometry, as well as the detection of video forgeries. One of their areas of expertise is forensic investigations of CCTV hacking.
In recent years, IPSC has joined Interpol’s «Cooperation with the Private Sector, Public-Private Partnership» project, in which it provides intelligence and investigative forensic assistance to police and law enforcement agencies in Israel and abroad.
The following investigation was conducted for all Israeli security services to understand whether security systems were breached by hackers and to prevent similar hacking incidents in the future. The digital investigation was conducted by a qualified forensic expert. The investigation is divided into two parts: part A deals with the hacking of surveillance cameras and part B deals with the hacking of WhatsApp messages.
For many reasons we cannot publish the entire report at our disposal, so we publish excerpts from it.

Digital forensics report
CCTV hacking and WhatsApp intrusion
22.10.2023
IPSC Forensic OSINT Investigation Report
(Hebrew translation)
«We found unequivocal evidence that the surveillance cameras were indeed hacked! Videos from the hacked cameras were posted by Arab hackers on Iranian and Russian social media. We found clear cooperation between Russian, Palestinian, and Iranian hackers in developing the methodology and practicalities of hacking. We also found that the data of all WhatsApp users in Israel (more than 5.5 million) is in the hands of hackers and for sale. The stolen WhatsApp data of Israeli users includes the details of Israeli government ministers(!) and their QR codes.
We believe that for reasons of state security, the use of this app should be banned or at least minimized for military and police officers, security personnel, and ministers: this app has effectively become a hacking tool.
After conducting an investigation, we realized that a forum of digital security officers/managers and a forum of investigators for internal digital investigations need to be established in Israel. We emphasize the need to develop practices and tools for cybersecurity and digital protection of facilities and infrastructures in Israel.»
What follows in the report is the testimony and details of the investigation given under oath by a forensic investigator. This is an important detail and demonstrates the significance and official status of the document. (CDN)
OSINT forensic investigation
«References: the Evidence Act [New Edition], 1971.
Name of Expert: IPCS-BWG Group
Address: IPSC-BWG
I, the undersigned, a forensic investigator and expert witness, give a digital forensic report on this matter:
Digital Forensic Examination of OSINT — the ability to hack surveillance camera systems, including video sharing, and the ability to hack Israeli WhatsApp subscribers.
I give this forensic report as an opinion and not as testimony in court, and state that I am well aware that for the perjury provisions of the criminal law, this report, signed by me, is legitimate testimony in court.
The data upon which the test is based:
On October 7, 2023, at 06:30 a.m. on Shabbat morning, Hamas launched a surprise attack on Israel. According to videos released by Hamas, surveillance and fire systems were neutralized by drones or anti-tank weapons. The barrier fence was blown up and destroyed by tractors in several places, and Hamas terrorists penetrated another fence on their way to the crossings.
The fact that the security forces were not prepared for a Hamas attack on Israel raised the following questions:
Is it possible that the surveillance camera systems were hacked and the video recordings made by these cameras were destroyed or replaced with fake ones?
Is it possible that in addition to monitoring and observing the location of IDF patrols in the border area, Hamas hackers managed to hack into the iPhones and smartphones of soldiers and security forces?
Action required
To conduct this investigation, I had to perform digital intelligence operations, including conducting digital reconnaissance on the Darknet and the regular Internet.
Part 1 — Hacking surveillance cameras in Israel
During my Darknet investigation, in incognito mode, I infiltrated sites in three languages that I am fluent in — Hebrew, English, and Russian.
For the Persian and Chinese sites, I had to use Google Translator. It’s worth noting that Russian, Hebrew, and English sites offer a lot of useful information on the Darknet, while on the regular Internet, you can visit Persian and Chinese sites and use Google Translator without revealing the true identity of the digital explorer.
During the covert operation, I managed to infiltrate two closed forums of Russian hackers on the Darknet. The first forum is «VLMRAMP» and the second is «Code by DarkWebForum» [Images 1, 2 for example].
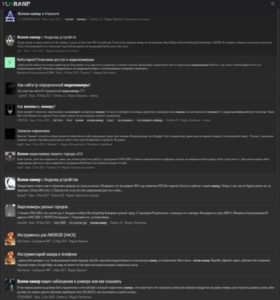
Image 1: Screenshot of «VLMRAMP», a closed forum for Russian hackers on the Darknet
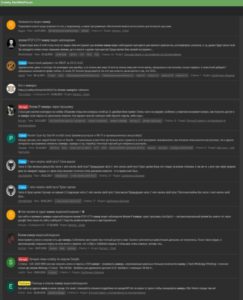
Image 2: Screenshot of «Code by DarkWebForum», a closed forum for Russian hackers on the Darknet.
On the VLMRAMP forum, I found a user page under the nickname «IT UNDERGROUND». On 09.10.2023 he posted a thread on the forum titled «Hacking surveillance cameras in Israel» [image 3 for example].
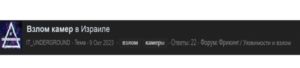
Image 3: An enlarged screenshot of a post on the topic «Hacking surveillance cameras in Israel» (in Russian) on the «VLMRAMP» forum on Darknet
The user «IT UNDERGROUND», who is also one of the moderators of the «VLMRAMP» forum, claims that IDF security cameras at the border were hacked using camera hacking techniques developed by a group of Russian hackers called «IT UNDERGROUND», which he heads. As proof, the hacker published a brochure in Russian on methods for hacking into surveillance cameras, as well as screenshots of translations of the brochure: For Arabic and Persian [images 4,5 for example].

FIGURE 4: Screenshot of a brochure on surveillance hacking techniques developed by the Russian hacker group «IT UNDERGROUND» titled «Hacking Surveillance Cameras» in Arabic.

FIGURE 5: A collage of screenshots of a booklet on surveillance camera hacking techniques developed by the hacking group: the Russian «IT UNDERGROUND». The title is «Surveillance Camera Hacking» in three languages: Russian, Arabic and Persian.
It is important to note that the surveillance camera hacking methodology of the Russian hacker group «IT UNDERGROUND» also includes methods for detecting hidden cameras and methods for sharing video recordings in surveillance camera systems, [images 6,7 for clarity].
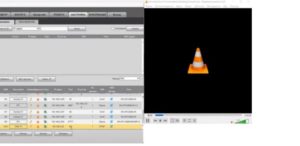
Image 6: Screenshot from a booklet on surveillance camera hacking techniques developed by the Russian hacker group «IT UNDERGROUND», here it is one of the methods of video sharing
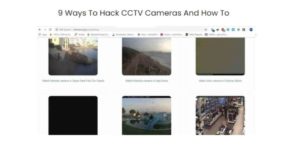
Image 7: Screenshot from a booklet on surveillance camera hacking techniques developed by a group of Russian hackers called «IT UNDERGROUND», which talks about 9 ways to hack into cameras and alter video images.
In the «Code by DarkWebForum» forum, I found the user page of «Anonymous». On October 25, 2022, he posted a thread on the forum titled «Hacking RTSP CCTV Cameras» [Image8 for an example].

Image 8: An enlarged screenshot of the «Hacking RTSP CCTV Cameras» thread post (in Russian) on the Darknet in a forum called «Code by DarkWebForum».
In a post dated October 25, 2022, user «Anonymous», who is also one of the moderators of the «Code by DarkWebForum» forum, details methods for hacking surveillance cameras, including methods for detecting hidden cameras and methods for replacing video recordings in surveillance camera systems. «ANONYMOUS» proudly and boastfully described his collaboration with groups of Arab and Iranian hackers and the fact that the Moses Staff group is using his methodology to hack Israeli security cameras. Like IT UNDERGROUND, Anonymous published a brochure on surveillance hacking techniques in Russian, as well as screenshots of Arabic and Persian translations of the brochure [images 9, 10 for examples].

Image 9: Screenshot of a booklet on surveillance camera hacking techniques developed by Russian hacker «Anonymous», with Arabic inscription «Security Camera Hacking».

Image 10: A collage of screenshots of a booklet on surveillance camera hacking techniques developed by Russian hacker Anonymous, with the title «Security Camera Hacking» written in three languages: Russian, Arabic, and Farsi.
It should be emphasized that Anonymous, in one of its texts, gave a detailed analysis of how the Moses Staff hacking group hacked Israeli surveillance cameras in November 2022 and noted the high professionalism of the hackers’ actions [Image 11 for an example].

Image 11: A photo from a surveillance camera in Jerusalem hacked by the Iranian hacking group Moses Staff in November 2022
I have conducted an investigation trying to find out the true identity of the users known by the aliases «IT UNDERGROUND» and «Anonymous». So far I have not been able to establish their true identity, but I have been able to find reliable information and establish that the user «IT UNDERGROUND» leads an independent anonymous hacker group with that name, and the user «Anonymous» leads a separate group of Russian-speaking hackers called «We are Anonymous».
I found reliable information that the hacker group «IT UNDERGROUND» is an autonomous contractor of The Internet Research Agency, which is the hacker division of the Wagner Group.
Our information: The Internet Research Agency, also known as «Kremlebots», «troll factory», «Prirozhinskiye trolls», «Olginskiye trolls», and «Lakhtobots» is a subdivision of Russian special services engaged in disinformation, Kremlin propaganda, manipulation of public opinion. «Agency» uses fake accounts in social networks and online publications, forums, and video hosting sites to promote the interests of the Russian security services, mainly engaged in spreading Kremlin propaganda and disinformation.
In addition, I found reliable information that this group is linked to the Russian hacker organization Cozy Bear, which operates under the auspices of the FSB.
Our information: «Cozy Bear», also known as APT29, The Dukes, and others, is a hacker group working for the Russian security services. According to Western intelligence services, it operates under the auspices of the FSB of the Russian Federation. «Cozy Bear» specializes in extracting information necessary for the leaders of the Kremlin. The group’s victims are Western governments and related organizations: ministries, agencies, think tanks, and government contractors. They have also targeted the governments of CIS member countries, Asia, Africa, the Middle East, and international organizations.
On Russian hacker forums on Darknet, I received links to several Arab forums dedicated to hacking surveillance cameras. It should be noted that these Arab forums are on the open Internet [images 12, 13, 14, 15 for examples].
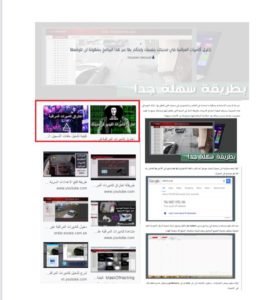
Image 12: Full-size screenshot of one of the Arab forums dedicated to surveillance hacking. The red bar indicates 2 brochures «Anonymous» (right) and «IT UNDERGROUND» (left) translated from Russian into Arabic.
Image 13: A close-up screenshot of one of the Arab forums dedicated to surveillance hacking.

Image 14: Close-up screenshot of an Arab forum dedicated to surveillance hacking.

Image 15: Close-up screenshot of The Hacker Academy, an Arabic forum dedicated to online learning, camera hacking, and security hacking. It is important to note that the forum operates under the auspices of the international hacker group Anonymous.
Several Arab forums and websites (including online media, YouTube, and the Al Arabiya network) have posted videos of Hamas terrorists infiltrating moshavs and kibbutzim, captured by Israeli surveillance cameras and hacked by Arab hackers.
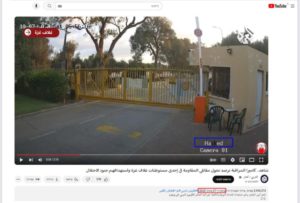
Image 16: A full-size screenshot of one of the Arab YouTube sites. On October 7, 2023 (marked by the red rectangle below), the site posted a video with the Arabic caption «Look: Surveillance camera follows our heroic resistance fighters as they roam a settlement near the Gaza Strip and seek to destroy the soldiers of the Zionist occupation» (Arabic translation). In the blue rectangle is the word «Hacked» and on the bottom right is the icon of the hacker group Anonymous. The logo of the Arab al-Arabiya television network is highlighted in red on the top left.
For some unknown reason, the hackers changed the time in the video to 05:56.

Image 17: Full-size screenshot: A collage of videos we shot documenting Hamas attacks on population centers near the Gaza Strip. The videos were hacked by Arab hackers from Israeli surveillance cameras installed in kibbutzim and villages, and posted on Arab forums and websites. The blue rectangles are labeled «HACKED.» In the photos, the icon of the hacker group Anonymous can be seen on the bottom right, and the icon of the Al-Arabiya network can be seen in red on the top left. For an unknown reason, the hackers changed the time shown in the video (in the pictures on the right) to 05:57.
Part 2 — Hacking WhatsApp
There is also a lot of information about WhatsApp hacking on Arab forums dedicated to surveillance hacking. These groups have a sub-forum teaching how to hack the app, as well as links to Arabic forums dedicated to hacking. [Image 18 for an example]. For more information on Arabic forums dedicated to WhatsApp hacking, please refer to the appendices.
Image 18: Full-size screenshot of one of the Arabic forums dedicated to WhatsApp hacking.
A few days after the Hamas attack on Israel, a pro-Palestinian hacking group released a statement in the media and on forums, announcing with great enthusiasm that the data of Israeli WhatsApp users had been hacked and that all of the user groups’ data was in their hands [images 19, 20 for examples].
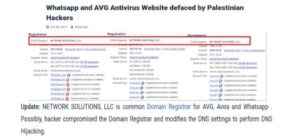
Image 19: Close-up screenshot of one of the articles about WhatsApp group hacks in Israel
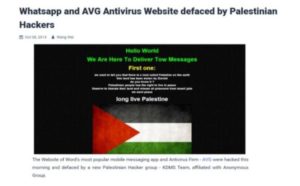
Image 20: Close-up screenshot of an article about WhatsApp group hacking in Israel.
Based on this information, I conducted investigative actions, which resulted in the following facts: In December 2022, WhatsApp user data from various countries, including data from 5,630,589 users from Israel, was offered for sale on the darknet [images 21, 22 for examples].
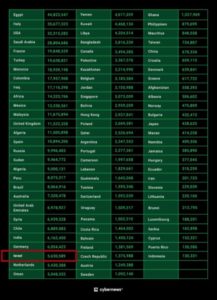
Image 21: Full-size screenshot of the number of WhatsApp users in different countries. The red square indicates the number of users in Israel.
According to the screenshot in image 21, the data of 152,321 Cypriot residents is also for sale by hackers (CDN)

Image 22: An enlarged close-up screenshot shows the number of WhatsApp users in different countries. The red box shows 5,630,589 users in Israel
It is important to note that WhatsApp’s darknet database also contains a QR code of the user, which allows one to join any particular user’s account from any computer, as well as from many models of smartphones. It is important to note that WhatsApp user databases went on sale in December 2022: the price of the user database from the US was 7 thousand dollars, the WhatsApp user database from the UK cost 3 thousand dollars, and the price of the user database in Israel was 3 thousand dollars. User databases have been sold on Darknet since January 2023 and actually to this day.
According to reliable information, databases of WhatsApp users, including a database of users from Israel, were bought on Darknet. It is known that Darknet recently sold WhatsApp lists with QR codes of Israeli politicians, high-ranking military officers, and businessmen for $150. [Images 23, and 24 are provided as an example].
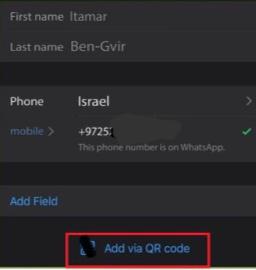
Image 23: Screenshot of WhatsApp user Minister Itamar Ben-Gvir. The red rectangle marks his QR code.
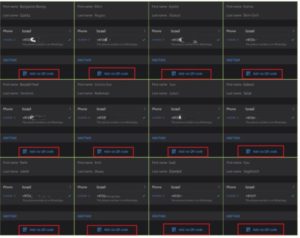
Image 24: Close-up screenshot: A collage we created of WhatsApp users, and ministers of the Israeli government. Their QR code is marked in the red rectangle.
It is important to note that among cybersecurity experts, WhatsApp has a bad reputation and is considered almost a hacking tool. For example, the International Cybersecurity Leadership Community Organization decided last year to stop using WhatsApp for cybersecurity reasons.
Conclusions
We found that security cameras and systems in Israel are not secure, we found unequivocal indications that security cameras were indeed hacked and their videos published. In the course of this investigation, we revealed the cooperation of Russian hackers with Palestinian and Iranian hackers on the development of methodology and practical techniques for hacking into security cameras, thus we exposed at least 2 groups of Russian hackers close to the Russian FSB.
We discovered that the data of all WhatsApp users in Israel, including government ministers, is in the hands of hackers and for sale. In our opinion, for reasons of state security, the use of this app should be banned or at least minimized for military, police, security personnel, and ministers, as this app has effectively become a hacking tool.
We recommend organizing a digital security service in Israel, both in the private and public sectors, by establishing a working group of representatives from the National Cyber Authority, Shin Bet, the IDF, the Israeli Ministry of National Security and Police, the National Cyber Security Authority (NCSA), representatives from the private security sector and representatives from cybersecurity and digital investigations.
Asher Ben Artzi
Chief Superintendent (Ret.)
IPCS — Black Wall Global
Digital Forensic Investigations Division
End of report.»
As stated above, the document was not published in full, but it is enough to leave no doubt about Russia’s involvement in the October 7 Hamas attack on Israel. The facts presented in the report directly point to the complicity of hacker groups affiliated with the Russian intelligence services in the attack on Israel and the lengthy preparations for it. Of particular concern are the facts of the involvement of Russian hacker groups in the process of training Arab and Iranian hackers in methods and techniques of hacking and penetrating the electronic and computer networks of Western democracies. There is no doubt that Arab and Iranian hackers operate under the control of the regimes of their countries and sooner or later use the knowledge received from their Russian colleagues against the civilized states of the West. The Kremlin leadership and Russian intelligence services encourage the close cooperation of the hacker groups they control with Iranian and Arab hackers as part of their hybrid warfare against the West. Israel and Ukraine are seen by the Kremlin as key targets in this war, so there is no doubt that Moscow will step up efforts to destroy them.
In the current circumstances, Ukraine and Israel, without exaggeration, are protective outposts of Europe and the entire Euro-Atlantic Civilization, protecting the West from barbaric, dictatorial regimes and Islamic terrorist organizations ready to destroy it, united in the «Axis of Evil»-Russia, China, Iran, North Korea, Hezbollah, Hamas, ISIS, PLO, Salafi Islam, Muslim Brotherhood, Islamic Jihad. Turkey is coming.
Against the background of the tragedy of October 7 and the results of the IPCS-BWG investigation, it is worth paying attention to a very important detail in our opinion. Since February last year, a lot of IT companies with hundreds of Russian IT specialists have moved from Russia to Cyprus under a special relocation program. We can assume with a certain degree of certainty that some of these companies worked in Russia with FSB licenses. With no less certainty, we can assume that together with their staff, some number of undercover officers of the Russian special services were «relocated» to Cyprus.
A powerful IT community with Russian roots and mysterious ties to Russia has emerged in Cyprus. This community is led by people who also have Russian roots and no less mysterious connections with Russia and Russian state structures.
Whether these roots and connections lead to hacker groups controlled by the FSB, GRU, and SVR remains to be seen.

