The cases are multiplying across Europe: Young men with pro-Russian views instructed on Telegram to carry out sabotage attacks. Western security officials point to the Russian special services. For this story, journalists went undercover to reveal how the recruitment works, writes OCCRP.
“Here’s an offer. Make a Molotov cocktail, go to the forest, and practice working with it. Send a video. Let’s start with this.”
“And the money when it’s done?”
“The money through crypto after a mission is done.”
This conversation — the apparent early stages of recruitment for a sabotage attack — took place on July 10 on Telegram, the popular social media and messaging service.
On one side, asking about the money, was Valeri Ivanov, a 26-year-old Russian-speaking Estonian looking to earn some extra money to supplement his income as a part-time land surveyor.
On the other side was an anonymous recruiter sitting behind a Telegram account called “Privet Bot” (“Hi Bot” in Russian).
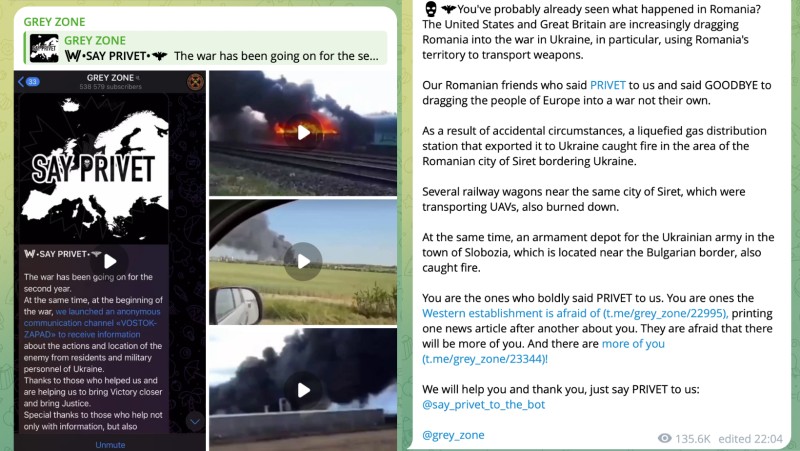
This account has been advertised at least eight times over the last year to the 550,000 subscribers to Grey Zone, the largest pro-Russian Telegram channel associated with the Wagner mercenary group.
The ads, which have also been shared on several smaller Telegram channels, Facebook, VKontakte, and even the popular gaming platform Steam, invite residents of European countries to join the fight against Ukraine’s Western allies.
“You’ve probably already seen what happened in Romania,” reads one ad posted on July 7 alongside video clips of several industrial fires that had purportedly been set by pro-Russian saboteurs. “They are afraid that there will be more of you. … and there are more of you.
“Just say privet to us.”
The sabotage footage isn’t real — the images all depict earlier, unrelated accidents. But this is the appeal that Ivanov answered.
After just a brief exchange, he was being encouraged to commit crimes in Estonia. Ivanov’s Russian-speaking chat partner offered him money to spy on military bases, set fire to NATO vehicles, and even commit murder at $10,000 “a head.” The recruiter’s demeanor was brisk, even rude at times, although some of his messages were incongruously accompanied by smiley faces.
Fortunately, Ivanov isn’t real. He was created as part of an undercover reporting project by journalists from Delfi, OCCRP, Paper Trail Media, ZDF, and Der Standard so that they could learn more about Russia’s efforts to recruit Europeans to commit acts of sabotage in their home countries via social media.
Security experts and intelligence officials say these efforts have ramped up recently, as Russia’s more sophisticated intelligence and security resources have been bogged down in prosecuting the Kremlin’s war in Ukraine and maintaining control over its occupied territories.
The most recent post on Telegram’s Grey Zone channel inviting readers to contact the “Privet Bot” account appeared on July 7. The post displays footage of purported sabotage in Romania that never actually took place.
“In the last two years there has been a huge increase in the number of sabotage attempts and acts in Europe, including such ‘dumpster’ operations,” said Indrek Kannik, the director of Estonia’s International Centre for Defence and Security. “This is terrorism in its purest form.”
He described the mass recruitment of saboteurs via social media as “trash fishing” since it yielded such low success rates — “but the resource costs are also minimal,” he explained.
Still, Russia appears to have had some successes. In recent years, citizens of Estonia, Germany, Poland, and other countries have been arrested, and in some cases convicted, of spying or carrying out attacks at the Kremlin’s behest. At least some of the perpetrators, including a group in Estonia, were recruited through Telegram and other social media channels.
And for every case that is successfully prosecuted, there are likely many more recruitment efforts that never come to light — especially on a platform like Telegram, which is widely used by the Russian military and state structures.
This August, its founder and head, Russian entrepreneur Pavel Durov, was arrested in France on charges of allowing the platform to be used for child pornography, drug trafficking, and organized crime.
Durov’s lawyer has described the accusations as “absurd” and said that Telegram abides by European law. After his arrest, Durov issued a statement acknowledging “growing pains” that enabled criminal abuses and pledging to improve the service. He is not known to face any accusations related to Russian intelligence services’ activity on Telegram, although French prosecutors did not respond to questions about his case.
The “Privet Bot” account has not been linked to any specific cases of sabotage. But when reporters showed “Ivanov’s” chat transcript to officials from five security agencies in Germany, Estonia, Austria, and Latvia, four of them confirmed that the interaction closely resembled cases they had encountered in which saboteurs had been recruited online by the Kremlin. (Latvia’s State Security Service refrained from commenting about the “Privet Bot” account, but said that Telegram had been used by Russian intelligence services in “several instances.”)
“So-called low-level agents are cheap, fast and safe,” said a source from one German security agency. “They often don’t even know who they are working for, whether it’s organized crime or a secret service. The long chains of middlemen make it difficult to attribute the recruitment to specific actors. All three Russian secret services would be capable of doing this.”
Marta Tuul, a spokeswoman for Estonia’s KAPO security service, said the goal of these types of attacks was to “cause fear, discontent, and confusion in society.”
«The success of an attack is not measured by the amount of property burned down or looted. It is enough for society to panic and doubt the functioning of the state.”
Kannik, the security expert, highlighted a more specific political goal. “Russia’s most important aim in carrying out sabotage,” he said, “is to create chaos and fear in Western societies — which will bring to power political forces that are prepared not to support Ukraine.”
Police investigating the car of Estonian Interior Minister Lauri Läänemets, vandalized by people recruited by the Russian security services, in December 2023.
Journalists reached out to “Privet Bot” directly to ask for comment. It did not reply in time for publication. The Russian presidential administration did not respond to a request for comment.
Durov’s lawyer also did not respond. But on September 23, the same day journalists contacted him and Telegram with their findings, Durov announced a new crackdown on Telegram. He said that the site had removed “problematic content” and updated its policies to clarify that it would share data with authorities “in response to valid legal requests.”
Meanwhile, Grey Zone, along with several smaller channels where the “Privet Bot” account had been advertised — and which were mentioned in journalists’ requests for comment — became partially inaccessible for users in multiple EU countries. The channels were still accessible through the browser version of Telegram, but were blocked for mobile or desktop app users with EU numbers. Those attempting to open them saw a message that they could not be displayed because they “violated local laws.”
In response to a request for comment, Telegram representative Remi Vaughn confirmed that Telegram had blocked these channels. “Content that aims to incite others to commit crimes breaches Telegram’s terms of service and so is removed whenever discovered,” he wrote. “Unfortunately, Telegram was never notified about these channels by any EU authorities through the DSA-mandated official lines of communication. Content reported properly is normally taken down within an hour.”
“Strengthening our moderation capabilities is Telegram’s main priority for the remainder of 2024,” Vaughn said. “Telegram is currently expanding its moderation teams and the range of organizations it cooperates with to combat abuse of its platform.”
Bot or Not?
‘We Pay Well’
Any reporting that involves deception requires careful consideration of journalistic ethics. In this case, editors and reporters decided that going undercover was justified because of the public interest inherent in investigating an apparent avenue of criminal foreign influence.
Not knowing how closely the fictional “Valeri Ivanov” would be questioned, reporters invented a full-fledged life story for him that included a family, a job, a hometown, and even hobbies. A credible account in his name was created on the Russian social network VKontakte, and a fake scan of an ID document was created for him.
Thus prepared, a reporter reached out to the “Privet Bot” account. As soon as he opened the chat window, pre-programmed menus asked “Ivanov” to choose the language he wanted to chat in and the country he was in.
He immediately received a welcome message in his preferred language, Russian. “Welcome, my friend! If you are reading this message, we have a lot in common. This means we want to be useful to our country and our peoples. Together we can stand up to the politicians who manipulate us.”
Prompted to begin chatting, Ivanov began with a simple greeting: “Privet.”
“Privet,” the account responded.
“I noticed your post and so I’m writing,” Ivanov continued. “I wanted to know if I can earn some money.”
“If you’re ready to work in Europe, then yes,” said the recruiter, and asked whether Ivanov was acting alone. Ivanov said he was.
“Too bad you’re just one,” said the recruiter. “You can do more with a group.”
Nevertheless, Ivanov was asked to provide his name, birthday, place of birth, and current location. He was asked for proof of his identity — he sent the fake ID photo — and questioned about his military experience. Ivanov said he had completed his mandatory service in the infantry, where he learned to shoot various weapons.
“What kind of grenade launchers?” the recruiter wanted to know. But Ivanov asked again about money.
“We pay well,” the recruiter replied, “from $10,000 per mission.” He asked Ivanov to confirm that he understood the «seriousness of the activities» and the «dangerous things» expected of him. “Have you ever killed? Committed any crimes?”
Then he turned specific. «Which task could you handle: Burn a Ukrainian military vehicle? Burn a truck carrying military equipment? Kill a fascist on Baltic territory?”
«The first two are ok,” Ivanov answered.
As a start, he was asked to practice with a Molotov cocktail. Reporters tried to continue the conversation along another track.
“How much to burn a car?” Ivanov asked.
“We’re interested in military objects and military equipment,” the recruiter clarified. “For a civilian car? That’s not even a mission. … If you burn a tank or an armored vehicle or a modern gun, I’ll give you 10K.”
“Look, if there’s some kind of radar station, that’s good too,” he added. “The best [equipment to destroy] would be NATO’s. But generally any [are good]. It’s a question of price.”
Since the recruiter had also mentioned murder, Ivanov asked how much he would be paid for that.
“There are many faggots in Estonia and the Baltics who desecrate the graves of Russian soldiers,” the recruiter responded. “10k per head.”
Ivanov wanted to know if there were any other ways to earn money.
«Look for fuel depots,” he was told. “Large civilian oil depots. Ukrainians can refuel there. Heavy trucks with tanks.”
When Ivanov said he didn’t know of any such facilities, the recruiter insisted he could find them: «Fuel is accumulated somewhere, which is later distributed to gas stations. It’s not a secret site.”
But he didn’t respond to Ivanov’s request for a specific address, instead asking his recruit to come up with his own targets. “Make a suggestion,” came the last message before journalists ended the conversation.
A Wider Pattern
The questions «Privet Bot» asked Ivanov provide insight into a Russian recruiter’s main points of interest about a would-be saboteur: Whether he has military experience and knows how to use weapons, whether he is self-motivated and willing to act independently, and whether he is prepared to undertake dangerous work.
A criminal background helps, too. As Richard Moore, the head of Britain’s foreign intelligence service, MI6, said in September at a public Financial Times panel, the Russians have resorted to hiring criminals out of desperation.
«They can’t use their own people, they’re having to do with criminal elements. Criminals do stuff for cash. They are not reliable, they are not particularly professional and therefore usually we are able to roll them up pretty effectively,» Moore said.
Though both Ivanov and his recruiter used anti-Western language, there was no explicit political discussion: The potential recruit’s pro-Russian attitude appeared to be taken as a given, or seen as inessential.
KAPO, Estonia’s internal security service, has some experience with pro-Russian sabotage. Earlier this year, the agency arrested over a dozen people accused of taking orders from Russian special services, some of whom went on to vandalize national monuments and cars belonging to the interior minister and a journalist.
Nine suspects in this case have already been convicted, according to KAPO, although the agency would not specify the charges. Another eight are now on trial.
KAPO officials declined to comment specifically on the “Privet Bot” account, but said Telegram was a popular recruitment venue for the Russian special services.
“We monitor what’s happening there and pay special attention to the active people,” said Marta Tuul, a spokeswoman for the agency. “Most of the collaborators are people with a previous criminal background and people living in deprived circumstances. They’re motivated by money.”
Estonia is not the only country to experience a rash of Russian-ordered attacks in recent years.
In neighboring Latvia, young men were recruited in 2022 to spy on a NATO air base, vandalize an Estonian military complex with graffiti, and allegedly commit arson in Ukraine. They were convicted of espionage in January. According to the guilty verdict, they were working for Russia’s military intelligence agency (GRU) — and case materials seen by reporters show they were recruited on Telegram.
The wall of an Estonian military complex vandalized by two young men recruited on Telegram in Latvia. The graffiti, reading «Killnet hacked you,» references a pro-Russian hacker group. Several Estonian institutions, including a NATO Cyber Defense Center housed here, had just experienced a sustained cyber attack.
In a separate case, two men are now on trial for allegedly attempting to set fire to the Latvian Occupation Museum, an institution that devotes most of its exhibits to cataloging the repressions visited on the country from Moscow during the Soviet era. They were also allegedly recruited via Telegram.
According to the Latvian security service, attacks like these are meant to sow divisions and “create an illusion that there is meaningful ‘underground’ support for Russia within Latvian society.”
In Poland, a group of people arrested last year were accused of spying for Russia and attempting to sabotage trains carrying weapons and aid to Ukraine. According to officials who spoke with the Washington Post, Russia did not want to rely on professional operatives for this operation and instead recruited people on Telegram, among other techniques.
And in Germany, the Federal Prosecutor’s Office announced in April that two German-Russian citizens had been arrested on suspicion of planning bombings and arson attacks at industrial and military sites, including U.S. military bases, and of maintaining contact with Russian intelligence.
Officials in these cases have not provided specific evidence of involvement by the Russian security services. But Dossier Center, an independent Russian media outlet, obtained documents earlier this year showing that a special unit of Russia’s military intelligence agency, the GRU, had repeatedly organized acts of sabotage in Europe, recruiting perpetrators through social media.
A representative of the Latvian State Security Service told reporters they expected Russian sabotage attempts to continue across Europe — and that Durov’s arrest would have “no impact” on the Telegram as a vector for recruitment.